
Our 4 step guide to cybersecurity content marketing
Table of Contents
- Four steps to content marketing for cybersecurity companies
Whether they working for a solution or service vendor or an MSSP, cybersecurity content marketing teams are in the deep end of the B2B tech marketing pool.
The security space is acronym heavy, crowded, and full of highly skeptical buyers who expect you to know your XDR from your EDR before trusting your product to stop cyberattacks.
Taking a generic approach to cybersecurity marketing will sink your cybersecurity company's campaigns faster than you can figure out what FIPS PUBS stands for. (“Federal Information Processing Standard Publication,” if you're wondering.)
The good news is that with a proper cyber security content marketing strategy in place, those responsible for marketing cybersecurity products can do a lot more than just tread water.
Learn more: See a selection of cybersecurity content marketing case studies
Or contact us for more examples of how we help cybersecurity with content marketing.
A successful cybersecurity content marketing strategy is an industry-specific approach to engage decision-makers with convincing messaging.
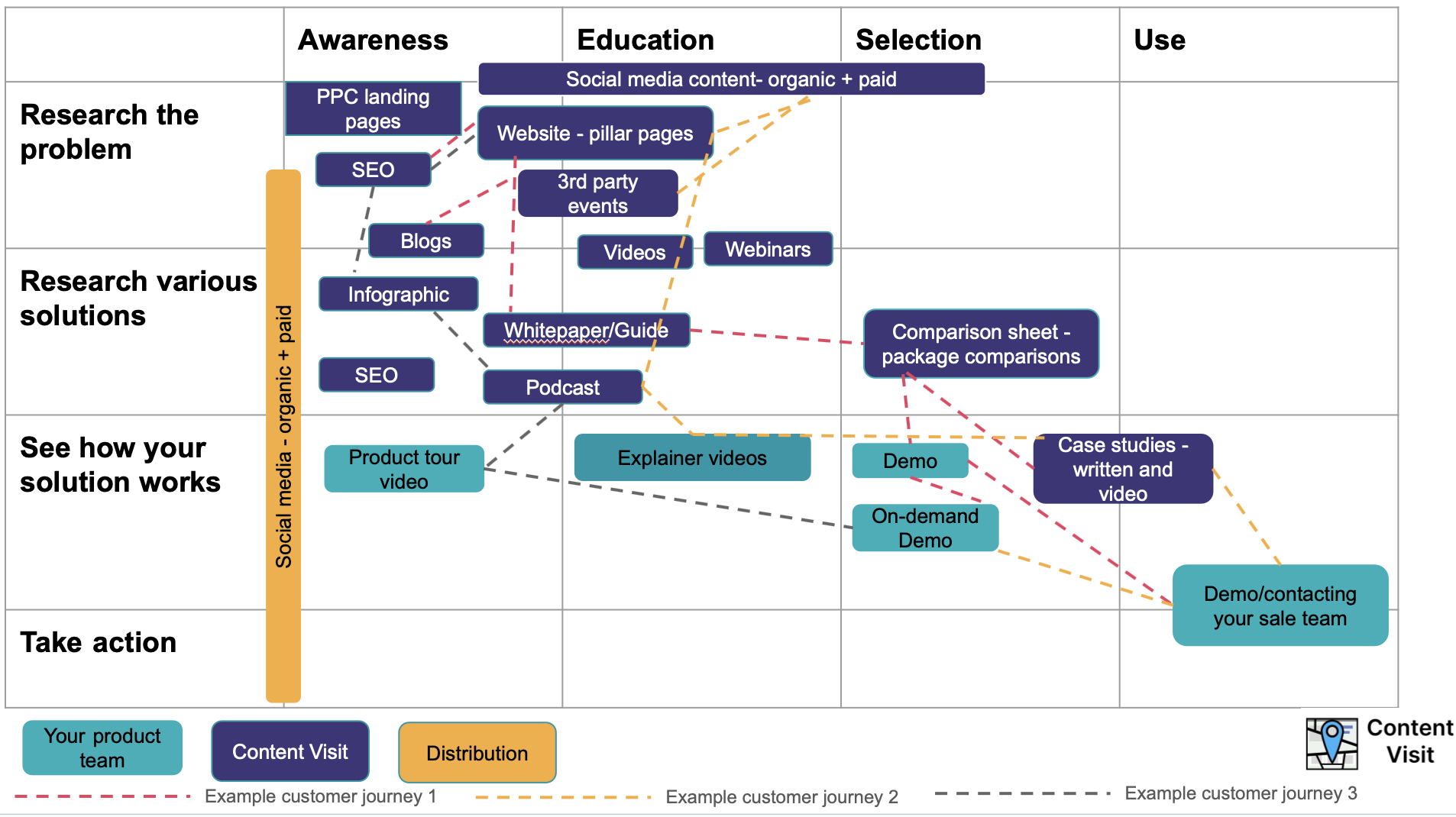
The image above illustrates cybersecurity content marketing funnels.
Here is our four-step guide to developing a content marketing plan for cybersecurity marketing teams.
Four steps to content marketing for cybersecurity companies
1. Find Content-Market Fit
Cybersecurity content marketing only works when marketers working with cybersecurity company understand exactly how their company's products/services fit into the broader security solutions marketplace.
In the wider business sense, this concept is called product-market fit, an idea described in 2007 by legendary Silicon Valley VC Marc Andreessen. At the time, he described product-market fit (i.e., having the right product for the right market) as being the “only thing that matters” for start-ups.
A similar theory applies to content. We call this “content-market fit.”
You can have the best white papers, blog posts, infographics, and webinars in the world. But if they don’t feature the kind of content your target audience needs, your content marketing efforts can still fail.
When it exists, content-market fit is obvious. It happens when your content is shared online by other people, starts ranking highly on search engines, and is a powerful lead generation tool.

In the cyber security industry, achieving a content-market fit means being able to answer these four questions:
What benefits do your cybersecurity solutions deliver to your customers?
What are your potential customers' pain points?
How do your solutions fit into the current threat landscape?
How solution/problem aware are your customers?
This exercise will help you spot the content gaps your efforts can fill.
There are always content gaps in a space as fast-moving as cybersecurity. None of your buyers will have a complete understanding of either their problems or the kind of solutions they need to improve their security posture.
Knowing exactly what these content gaps are is at the foundation of any good cybersecurity content strategy.
2. Research Your Cybersecurity Company's Audience
Once you understand the content gaps that exist within your market, the next step towards a successful cyber security content marketing campaign is to learn about the humans that will consume your content.
This is where cybersecurity marketing personas come in.

Do you know who your business’s ideal customers are?
What are their:
Job titles
Biggest challenges
Past experiences with solutions like yours
Levels of solution and problem awareness
Goals with a product like yours
Greatest concerns right now?
The more human you make your buyer personas, and the more you know about your audience, the easier it will be to create content they can relate to.
For example:
Which persona is easier to create content for?
1. Solutions architect at a mid-sized fin-tech in the EMEA market.
or
2. Joe, a 45-year-old first-year solutions architect at a fast-growing European fin-tech, who is worried about how his team is going to protect all of the cloud workloads that his company keeps spinning up.
Audience research and customer personas are not a one-time thing. People change, and personas should too.
Changing environments and business conditions can cause dramatic shifts in people's working lives, challenges, and aspirations.
For example, your customers' security concerns will be a lot different today than in 2020, when they were in the middle of a pandemic.
Talk to your existing customers directly if possible, interview your sales team, your CEO and get as much information from your marketing and sales leadership team as possible.
Do this alongside SEO keyword research to better understand how people explore the web looking for products like yours. Its also a good idea to visit forums and B2B social channels like LinkedIn to check out what your audience is talking about between themselves.
You can learn more about how to research your customers in our guide to cybersecurity SEO.
3. Plan, Write and Design Cybersecurity Content
Once you know what your content will do (content-market fit) and who will engage with it (personas), you can start planning how to create, distribute, and measure it.

You also need to know what resources you have. For example, budget for writers, designers, and SEO tools, and whether you can contact internal technical experts for consultation on content.
Learn more: how to create helpful content
Speaking of resources, artificial intelligence chatbots like ChatGPT can help you gain insights from reports and surveys, but they're not necessarily good for content creation.
Tip: Before you plan a content calendar, audit your existing content. To do this, make a spreadsheet that includes a link to every piece of content on your website, its purpose (i.e., bottom of the funnel sales, sales collateral, etc.), its publishing date, format, when it was last revised, who owns it, and its target keywords (if applicable).
To plan content, you also need to have clear goals for different content assets as well as your overall GTM strategy.
A common cyber security content goal is to improve search engine rankings on traditional search engines like Google and AI search engines like ChatGPT and Perplexity. Another content goal could also be to boost brand recognition, establish thought leadership in a certain sector, or increase conversion rates.
Learn more: 9-step SEO content marketing playbook
You might also want to fill content gaps that product and sales teams have identified. Or power your GTM stratagy.
To do this, you need a :
content planner
content calendar.
Cybersecurity content planner template
A cyber security content planner will give your team a place to coordinate work.
It can be shared with other stakeholders in the content production process, such as writers, designers, and product marketing teams.
A content planner’s headers might look something like this:
Title Brief Outline Draft Owner Notes Due
A content planner can give you a high-level overview of what your content is going to do. It can also tell you what kind of relevant content you need to engage your target customers.
Cybersecurity content calendar checklist
A content calendar helps you see what’s coming up.
It should include the :
A list of the content assets your team is working on (or will work on soon).
When these content assets should be completed.
A checklist for ensuring that all the correct attributes (design, meta description, email copy, etc.) are present.
A content calendar is something you can share with your internal team and any relevant contractors.
You might also augment your calendar with project management tools like Trello or Asana to plan and manage your content production efforts.
Tip: Content teams often get confused when using various tools or spreadsheets at the same time. It’s a good idea to limit team members to one system at a time, i.e., a kanban board or Google Sheet.
Once you have an effective system for managing content planning and production, you need to harness the means of content production. Namely, you need at least one cybersecurity writer and designer.
Learn more: Our guide to hiring and leveraging a cybersecurity writer
To make it easier for your team to produce content, it is also worth investing in content optimization tools such as Clearscope (to make sure your writers hit the right keywords) and Grammarly (to ensure content quality).
AI content production tools such as Chat GPT can be useful for content ideation and creating outlines. However, you should never publish content from these tools on your webpage.
Cybersecurity Content Examples
The cybersecurity content your organization produces is going to be totally unique. However, to inspire you here are a few examples of security content (including blogs, infographics, and whitepapers) assets we have worked on in the past.
This blog about how much a business should spend on cybersecurity works well because it puts key information about security spending in bullet points at the start.
A comparison table like the one in this blog comparing DSPM vs CSPM tools shows potential buyers the advantages and disadvantages of your solution versus alternative solutions in a fair and transparent way.
An easy-to-find section on your webpage explaining to prospective customers what your integrations are and what integrations you don’t have yet but are working on soon.
Content on your website with first hand advice, based on your experience, about a technical query. For example, “Can you use x solution in y environment?” like this blog about using network detection and response tools to protect remote workforces.
An article that helps people concerned about identity theft figure out how to delete themselves from Google such as this article.
A whitepaper aimed at a very specific security solution use case or benefit proposition (not a generic) one like this whitepaper about using AI to save money in your SOC.
4. Distribute Engaging Content
Even the best content won't deliver results if it doesn't get in front of the right audiences.
Here are four methods that cyber security marketing teams can use to distribute content (for more, read our blog post on 8 B2B content distribution channels).

Cybersecurity Guest posting
Getting your cybersecurity writers to work with your subject matter experts (SMEs) and ghostwrite articles on third-party sites is one of the most effective content outreach techniques.
Websites such as Dark Reading and HackerNoon are always open to contributions from industry experts on topical issues.
Learn more: 31 no-cost cyber security marketing guest post opportunities
You more than likely have access to cyber security SMEs within your organization. Pair these individuals with a cybersecurity writer to pitch and write articles for placement on other sites.
If allowable under the site's terms of submission, you can use guest posts to link back to content assets on your website.
Social media
B2B marketers can use B2B social media marketing, i.e., posting on LinkedIn, to share content via newsfeed posts.
To share content through LinkedIn posts:
Pick a talking point from your content.
Break it up into short one/two sentence paragraphs.
Link to your article in the comments section of your post with “to learn more, check the link in the comments section.”
For example, if you wanted to distribute a blog post about five security challenges healthcare security teams face, you could create a LinkedIn post where you list the five challenges and write an introduction that explains how you know this.
“We spoke to two dozen healthcare CISOs about their main challenges, and these were the top 5…..”
This lets readers know you did your research and sparks their interest in learning more.
Cybersecurity Email marketing
There are two ways to distribute content through emails:
1. Through a newsletter people subscribe to (or one that goes out to existing clients)
2. Via cold email as part of your sales outreach efforts.
To distribute content through a newsletter, give your readers a conversational entry point into whatever it is you want to say.
Learn more: How to write a B2B newsletter in 5 steps
Your newsletters should ask questions that lead your readers into them organically and attract attention back to the content you want them to see.
Tip: Use questions for subject lines and preview your email content. Don’t be afraid to use attention-grabbing statements, like “We spoke to healthcare CISOs, and this is what we learned.”
Content can also help boost your email outreach efforts. Pitching prospective customers with something that gives them value, i.e., an article you published that they might learn from, can help spark conversations.
Cybersecurity SEO
You can driving traffic through search engine optimization (SEO) to your content. Even in the age of Search Engine Generative Experience (SGE), B2B SEO is still one of the most powerful marketing channels in existence.
Read a cybersecurity SEO case study
The most important SEO factor for Cybersecurity content success however is be super precise. Optimize content (using meta descriptions, headers and title tags) for low volume, high intent searches.
For example, instead of trying get get searches for a term like "Antivirus" go for more specific terms like "antivirus solutions for schools" that also tie in with ICP pain points i.e the exact problem your audience is trying to solve.
Set Clear Goals, And Measure Results
Content can deliver measurable ROI for digital marketing teams by generating and converting leads.
To get results from content marketing, you need to measure outcomes.
You have to define your content marketing goals. Separate clear goals for content from fuzzy ones.
For example:
Increasing website traffic is a fuzzy goal. Growing the number of first-time visitors to our website’s blog by 50% by Q4 is a clear goal.
Other clear goals include:
Increasing the conversion rate for website visitors signing up for our newsletter by 2%.
Growing the download rate for our case studies by 10% before Q3.
Having 2% of all second-time visitors to our website try a product demo for the rest of the quarter.
Driving a 4% increase in the number of leads coming from our newsletter by Q1 next year.
These clear goals have three things in common. They are specific, measurable, and they drive business growth.
They are not vanity metrics. Vanity metrics for content are statistics that look good but don’t indicate whether or not your content is helping your organization grow. For example, visitor traffic (on its own) can be a vanity metric.
It’s OK to say that traffic is going up. But what kind of traffic is it, and is the increase in visitor numbers actually contributing to your business in any measurable way? Are visitors staying on your site and going elsewhere after they land? If not, it's time to rethink your goals.
9 Best Cybersecurity Content writers for Hire in 2025
This is our current list of cybersecurity content writers based on extensive online research and our own networks. Over the past five years, we’ve looked at hundreds of writers' CVs and offers. Here are nine that stood out to us.
Laura Martisiute/Content Visit
Literally us. The founder of Content Visit, Laura, has worked with IBM, created and managed the creation of the majority of content for the past five years at DeleteMe, and wrote content and copy for Randori, Morphisec, Element Security, and many other cybersecurity companies.
Check out her content writing references on Linkedin.
Services: Read them here.
Clients: Seed to Enterprise level.
Website: You’re on it right now.
Pricing: Starting at $1000 a month.
Karen Walsh / Allegro Solutions
A non-practicing attorney and former internal auditor providing expert cybersecurity content that aligns with compliance and marketing needs.
Services: Marketing content, messaging, compliance-focused content.
Clients: Seed to Series B companies that need content without in-house resources.
Website: allegrosolutionsllc.com.
Pricing: You can see Karen’s pricing sheet here. Her general rate is currently quoted at $125 per hour. A blog post is around $600.
Amanda Scheldt
A cybersecurity consultant and content writer who helps early-stage startups craft technical and engaging content.
Services: Content writing, security consulting.
Clients: Seed stage and Series A SMBs that need content support
Website: infinitycontentsolutions.com.
Pricing: Contact for pricing.
Pete Hugh
Pete claims to offer expert-level writing that generates leads, supports sales, and builds trust with infosec leaders without relying on internal SMEs. Their services include white papers, case studies, research reports, web content, and full content strategies. They work exclusively with ambitious, intellectually honest clients who challenge industry norms and strive for measurable results.
Services: white papers, case studies, research reports, web content, and full content strategies.
Pricing: A call with Pete is $350, and he will probably tell you his pricing from there.
Ian Correa
A cybersecurity content writer specializing in engaging short- and long-form content to drive conversions.
Services: Cybersecurity content creation to boost traffic and revenue.
Website: See his LinkedIn Profile.
Pricing: You'll need to contact him to get up-to-date pricing.
Lea Rabinowitz/&content marketing
A marketing strategist and writer helping cybersecurity companies with inbound marketing and content strategy. Lea has an impressive portfolio; you can see some of her recent examples here. She does not list her pricing or specifically offer cybersecurity copywriting.
Services: Inbound marketing, content writing.
Website: andcontentmarketing.com.
Pricing: We couldn’t find Lea’s pricing online.
Lewis Commercial Writing
Lewis Commercial Writing is an Austin-based cybersecurity copywriting and content design studio. They do website copy, white papers, and case studies. We like their different copywriting sprint offers that might fit companies unsure of their exact goals.
Services: Technical copywriting, website copy, landing pages, etc.
Website: https://www.lewiscommercialwriting.com/cybersecurity-copywriters.
Pricing: You’ll need to contact them for pricing.
Sara J. Nguyen
A freelance writer specializing in SEO-driven content for cybersecurity and B2B SaaS companies.
Services: SEO content writing, case studies, white papers, blog posts.
Website: sarajnguyen.com.
Pricing: From Sara’s pricing page:
Standard Blog Posts: StartS at $500.
Case studies (SME interviews included): Starts at $1,500.
Whitepapers: Starts at $1,500.
Rodika Tollefson
Rodika Tollefson is a seasoned technology and cybersecurity writer with a background in journalism. With 25 years of experience, she has worked with businesses of all sizes, from startups to Fortune 500 companies. She does journalism, copywriting, and brand storytelling.
Services: Copywriting, content marketing, ghostwriting, and brand journalism.
Website: https://seattletechnologywriter.com/.
Pricing: Not listed; you’ll need to ask her.
Alice Hollis
Alice is a copywriter with a lot of experience (150+ tech companies). We like her focus on positioning cybersecurity as a business enabler rather than just a risk.
Services: Various copywriting services including everything from email nurture flows to one-pagers and infographics. You can see her menu of services.
Website: https://www.alicehollis.co.uk/cyber-security-copywriter/.
Pricing: Her pricing starts at a day rate of £400.
Cybersecurity Content Marketing F.A.Qs
A few of the most common questions we hear from security brands thinking about doing starting a content marketing program.
How is cybersecurity content marketing changing in 2025?
With the majority (50%) of marketing teams increasing their budgets this year, we predict that cybersecurity companies will invest more in content marketing campaigns than in the past. Key areas of focus will be in high quality content to stand out from competitors using AI to produce large volumes of information. We predict that cybersecurity companies will increasingly win with target audience centric content.
Where should a cybersecurity content marketing program start?
The very first thing we would recommend a company to do is to figure out a few easy wins for a content marketing program and work backwards from there. Usually a good place to start is with search engine optimisation (or generative AI optimisation). Content can generate traffic, replace paid ad spend and increase engagement with your messaging. We recommend starting with a Cybersecurity SEO approach.
Can I use AI for cybersecurity content marketing?
Absolutely. But not to generate content. We strongly advise against using an LLM to generate large volumes of content assets in a B2B marketing scenario. Your buyers are highly likely to notice generic phrases or inaccurate claims in your content and your brand reputation will suffer as a result. We recommend using AI to track keywords, repurpose content assets and build efficiencies in the content ideation and research process. AI can save significant time but it is not a great replace for writing or thinking.
Do I need to hire a cybersecurity content writer?
Not internally. The best value method of building a cybersecurity content marketing program is outsource content writing and design to a freelance writer or a boutique cybersecurity content marketing agency. We cover some popular cybersecurity content writer options and pricing here.
How much does cybersecurity content marketing cost?
Typically between $2000 and >$10000 per month. Larger enterprises spend hundreds of thousands of dollars a year on content writing, design and distribution. You don't have to spend that much however. We recently surveyed 90 different cybersecurity marketing agencies for a pricing run report. Read about how much cybersecurity marketing costs here.
What's the ROI on cybersecurity content marketing?
Ideally more than 3x spend on content production. Measured by replacement add value, increased brand visibility, leads generated through content assets and a host of other KPIs that will depend on your exact goals.
Content Visit is a cybersecurity content marketing agency
It is possible to implement the four steps listed above with an in-house security marketing team.
However, for most cyber and information security companies, it makes more financial and operational sense to bring in an cybersecurity content marketing agency partner.
Contact us for more information
Written by Laura Martisiute